The Modular L1 Powering Chain Abstraction: Particle Network

Table of Contents:
Note: This article was updated on 15/05/2024 to refine the explanation of certain components of Particle Network, as well as reflect conceptual developments that have occurred since its original publication.
TL;DR:
- L2s and rollups deliver the scalability blockchains need, but resulting in siloed ecosystems. Meanwhile, cross-chain interactions are too costly and difficult, creating an undeniable industry-wide User Experience tradeoff.
- Particle Network’s modular L1 powers chain abstraction, making the experience of interacting with a multi-chain ecosystem invisible to users. It acts as a settlement and coordination layer for users across all chains, creating a multi-chain experience that resembles the unified liquidity and sovereignty of a single chain.
- Particle Network = Chain Abstraction = A seamless, universal Web3 UX.
- Particle’s Wallet Abstraction services boast 17M users, 900 dApps, and secure $2B across 56 chains, uniquely positioning us to enable chain abstraction.
- Through our rollout, all Particle Smart Wallets will be seamlessly onboarded into our L1, instantly upgrading them to Universal Accounts. This includes all Bitcoin wallets leveraging BTC Connect.
- Our L1 is secured via a dual staking system employing both the Particle Network Token, $PARTI, and BTC staking via Babylon.
- It also debuts aggregated data availability (AggDA) and reliability through the combined utilization of Celestia, Avail DA, and NEAR DA.
- Gas for all operations can be paid with any token, ultimately settled in $PARTI, which accrues value from the network’s usage.
- This L1 features a high-performance EVM execution environment and a modular architecture that makes it infinitely composable.
A broken ecosystem and user experience
The Web3 experience is far from feeling intuitive or universal.
L2 chains and rollups are quickly accelerating blockchain scalability, with new solutions hitting the market at an impressive pace. However, this results in siloed, incompatible ecosystems and user bases, fragmenting Web3, restricting its growth, and limiting it to technically-aware users and niche applications.
The solution? Chain abstraction. This refers to simplifying users’ interactions with blockchains, allowing them to use any product and asset without worrying about managing multiple wallets, bridging, underlying infrastructure, etc.
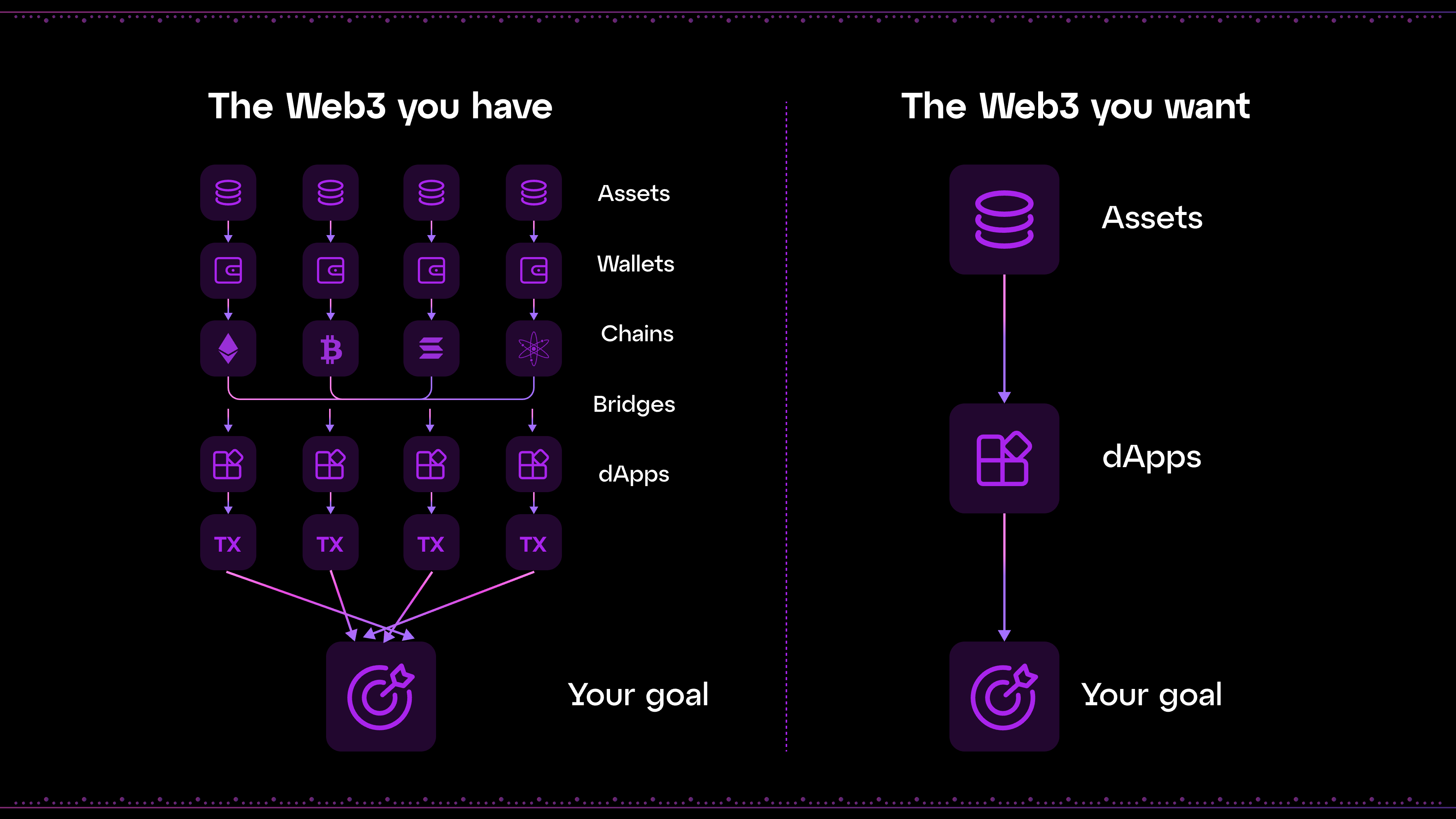
A fully chain-abstracted experience may look as follows:
- Alice discovers a Play-to-Earn dApp. The dApp is hosted on Arbitrum.
- Alice starts using the dApp. The assets in her wallet (Polygon-native) are used for basic dApp interactions. Bridging is automatic, executed atomically as she plays.
- After playing for a bit, Alice earns some tokens. She uses them to buy an NFT for her friend Bob’s birthday. Unbeknownst to her, the NFT is hosted on Optimism. She can seamlessly send it to Bob’s Universal Account. Importantly, throughout her whole experience, Alice has only used a single gas token.
- Bob decides to take a loan against the NFT on Solana and use the proceeds to buy a meme Bitcoin Ordinal. He does this in just a few clicks within a few minutes, all through the same account.
As you’re probably thinking, chain abstraction brings Web3 closer to Web2’s immediately gratifying, enticing experiences while maximizing the advantages of decentralized blockchain scalability and true digital asset ownership.
To modularly power chain abstraction and take Web3 to the next level, we are releasing the Particle Network L1: a Cosmos-SDK-based blockchain solving the multi-chain fragmentation of users and liquidity.
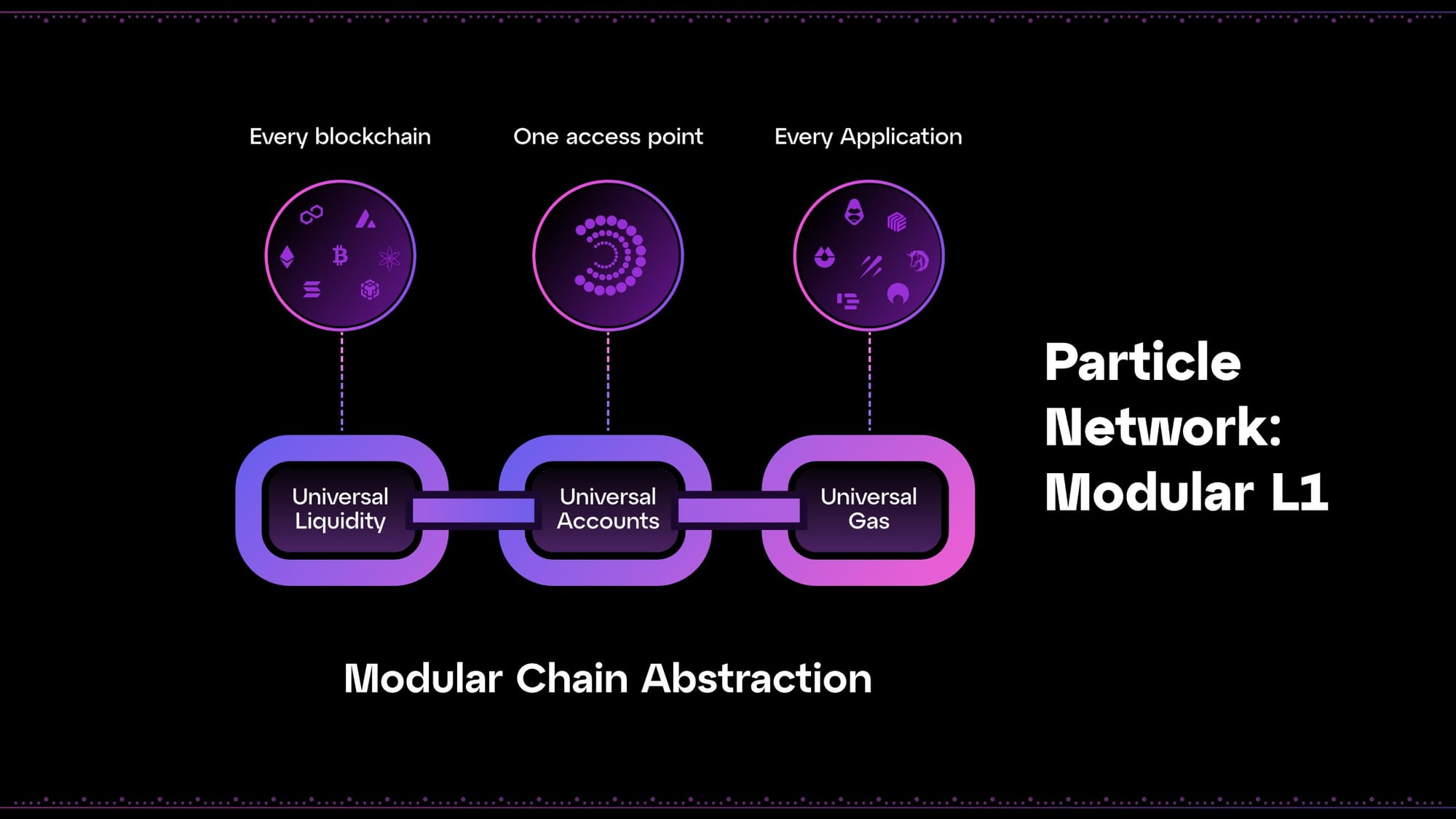
Introducing the Particle Network Modular L1
Particle Network’s modular L1 blockchain powers chain abstraction by creating Universal Accounts that give users a single address and interaction point across chains while abstracting gas and unifying liquidity. This empowers existing L1s and L2s with seamless coordination across ecosystems.
Relying on the Cosmos SDK to build this L1 allows us to make it intrinsically modular, retaining its sovereignty while outsourcing key functions like validation and data availability to specialized ecosystem actors. This is primarily driven by Modular Nodes, which help secure the network and allow for its decentralized operation through managing transaction validation, data availability, etc. Our L1 also provides a high-performance EVM execution environment, leveraging a Universal Inter-Blockchain Communication (IBC) protocol for interoperability, enabling cheap, fast cross-chain transaction execution.
Particle Network relies on three core modules, each creating a unique user advantage:
- Universal Accounts: These offer a single interaction point, user address, and balance across all chains, including EVM and non-EVM networks. With Universal Accounts, Particle Network proposes a new UserOperation structure, simplifying the management and usage of Smart Contract Wallets on all EVM chains and allowing them to control accounts on heterogeneous blockchains like Bitcoin and Solana.
- Universal Liquidity: Unifies the liquidity of all chains through the optimistic execution of cross-chain atomic transactions and swaps. This allows users to seamlessly interact with new chains, even if they don't hold tokens on them.
- Universal Gas: Allows users to pay gas for cross-chain transactions with any token, as opposed to the multichain ecosystem’s need for multiple units (SOL, ETH, MATIC, etc.)
All transactions are ultimately settled in $PARTI, Particle Network’s native token.
How does Universal Liquidity work?
To illustrate Universal Liquidity, the core functionality enabling Particle Network’s Universal Accounts and Universal Gas, let's consider the following example:
- A user wants to seamlessly purchase an NFT priced at $300 (in ETH) on Chain D using their USDT, which balance equally distributed among Chain A, Chain B, and Chain C.
- By clicking “Buy”, the user bundles UserOperations involving five chains (Chain A, B, C, D, and Particle Network) into a single signature sent to the Particle L1.
- Upon the execution of the above signature, the USDT on Chains A, B, and C is exchanged for an intermediary token, e.g. USDC, using the corresponding chains’ DEXs (Decentralized Exchanges).
- The USDC from Chains A, B, and C is sent to a Liquidity Provider (LP).
- The LP releases the USDC on Chain D.
- The USDC on Chain D is exchanged for ETH using a DEX on Chain D.
- The ETH on Chain D is used to purchase the NFT.
Note: For the sake of illustration, we’ve included the process of underlying swaps within this flow. However, operations including tokens that can be used for intermediary purposes (e.g. USDT) may not require swapping.
This process is diagrammed below:
In other words, the user engages in an atomic swap with the LP, exchanging their assets for the LP's intermediary token, which is then transferred to the LP. The LP then releases the intermediary token on the target chain (Chain D), which is exchanged for the target asset on the target chain. The LP in this context is not a traditional DEX LP providing liquidity for token pairs; rather individual providers that earn a small fee for every trade by facilitating the transportation of the intermediary token (e.g., USDC) across different chains.
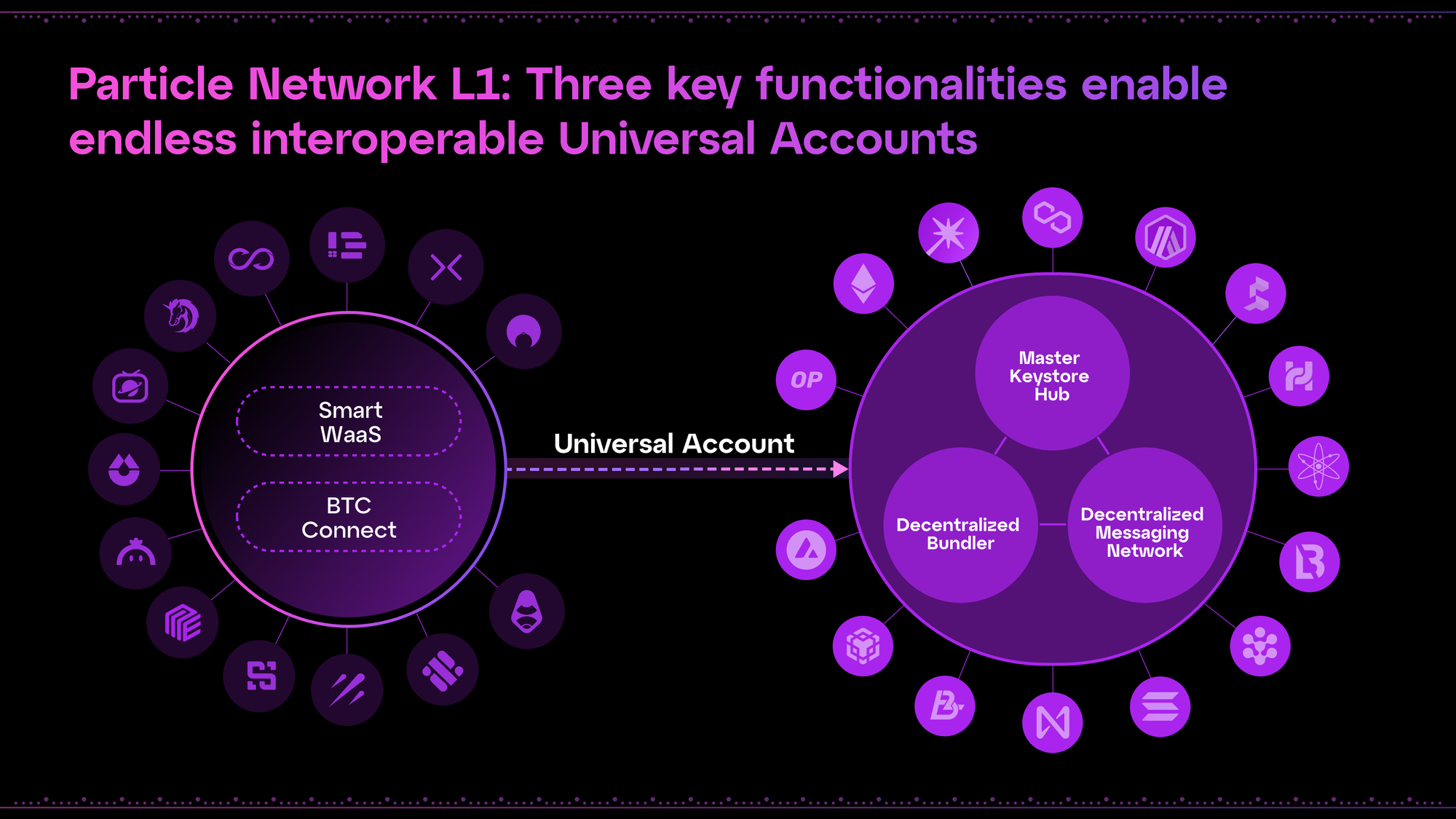
Core modules
Within this modular L1, the following core modules support the design and ongoing coordination of Universal Accounts:
- Master Keystore Hub: Particle Network acts as the central hub coordinating smart contract deployments and updates across all networks, automatically synchronizing settings between each Universal Account instance and ensuring complete state parity across networks. Account settings are stored on Particle Network to be used as a central source of truth across every instance. Our L1 then facilitates cross-chain messages to either deploy new instances abiding by these settings or update existing instances as these settings change.
- Decentralized Messaging Network (DMN): On Particle Network, Relayer Nodes use a Messaging Protocol to monitor whether UserOperations on external chains have been executed successfully, and then settle the execution status on our L1. This network of decentralized Relayer Nodes, tasked with monitoring external chain events and the settlement of state events, is called the Decentralized Messaging Network.
- Decentralized Bundler: While current implementations of Bundlers are centralized and as such censorable, Particle Network has designed and implemented a fully decentralized Bundler for high-volume UserOperation processing. Particle's Decentralized Bundler is used to initiate UserOperations on external chains, such as performing a DEX swap or purchasing an NFT.
Modular ecosystem onboarding
Our L1, with its focus on chain abstraction, leverages Particle Network’s existing Wallet Abstraction solutions: Modular Smart Wallet-as-a-Service (WaaS) and BTC Connect. These secure $2B across 56 chains, with 17 million users across 900 projects.
Modular Smart WaaS offers a highly customizable solution for developers to onboard users into their dApps using their Web2 accounts, as well as leveraging account abstraction (AA). Particle Network is a leader in the account abstraction field, facilitating 10M+ UserOperations across 36 chains, and in many cases acting as the single source of AA solutions within certain networks. Meanwhile, BTC Connect is the first AA protocol for the Bitcoin ecosystem, kickstarting Bitcoin’s path toward chain abstraction. This solution has been embraced by the most prominent Bitcoin L2s within the ecosystem and is set to upgrade millions of Bitcoin wallets to EVM Smart Wallets coordinated by the Particle L1, ultimately benefiting the Bitcoin network.
Particle Network’s architecture allows the Smart Accounts resulting from its existing solutions to seamlessly onboard into its new L1, becoming Universal Accounts. This will instantly allow them to settle and coordinate cross-chain operations on our network, also bootstrapping the chain’s initial ecosystem and traction.
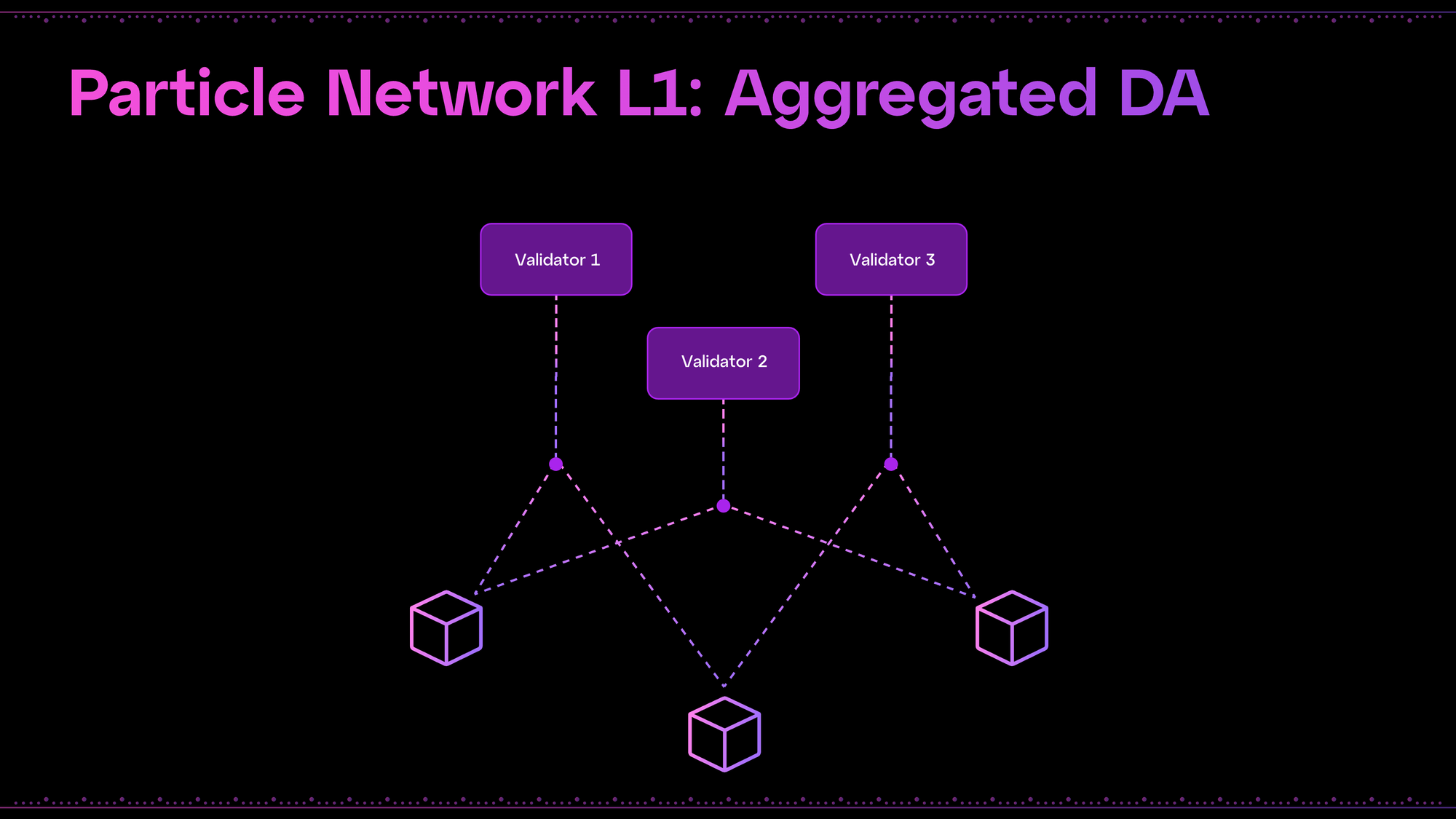
Design and security
The Particle Network modular L1 features a dual staking system, combining Proof-of-Stake through Tendermint with Bitcoin's native security and censorship resistance. Babylon's BTC staking facilitates this.
Our L1’s dual staking mechanism leverages two distinct pools of operators: one with delegations of Particle Network’s $PARTI, and another with delegations of BTC. Both groups are required to agree on validity individually, warranting equal participation in consensus.
Besides the above, Particle Network’s modular L1 will feature aggregated data availability (AggDA), relying on a combination of external providers. This will bolster performance, efficiency, and availability by conditionally alternating between selective and redundant publishing. AggDA takes advantage of the unique benefits and differentiators of various independent solutions, improving our L1’s decentralization, scalability, and performance. These external solutions, and their differentiators, include:
- Celestia, which features a vast infrastructure ecosystem, close ties with Cosmos (through its usage of the Cosmos SDK), and high throughput, making it an invaluable and crucial part of our DA stack.
- NEAR DA, which boasts impressive performance at a cost of roughly $0.0016 per block.
- Avail DA, a leader in DA decentralization with a vast feature set and quick verification time, which places it as an integral component of Particle Network.
Advantages of chain abstraction and next steps
Chain abstraction is the missing piece in the transition between Web3's early and mainstream stages. So far, the stages leading up to our industry’s current state can be regarded as follows:
- Stage 1: Early, decentralized L1s with concentrated liquidity and a self-contained UX, but without scalability capabilities. In this context, only financial applications can thrive, as other use cases get priced out as they scale.
- Stage 2: Competing L1s (some centralized) with different approaches to finality/scalability appear, fragmenting liquidity and user bases. New ecosystems arise, competing for projects and developers.
- Stage 3: Decentralized, scalability-oriented solutions combine to offer faster and cheaper transactions to existing ecosystems, but widen the interoperability breach across chains.
As Web3 gathers critical velocity, chain abstraction appears at the chasm of its growth curve, aiming to become the definitive solution for solving scalability and decentralization and granting users a better experience.
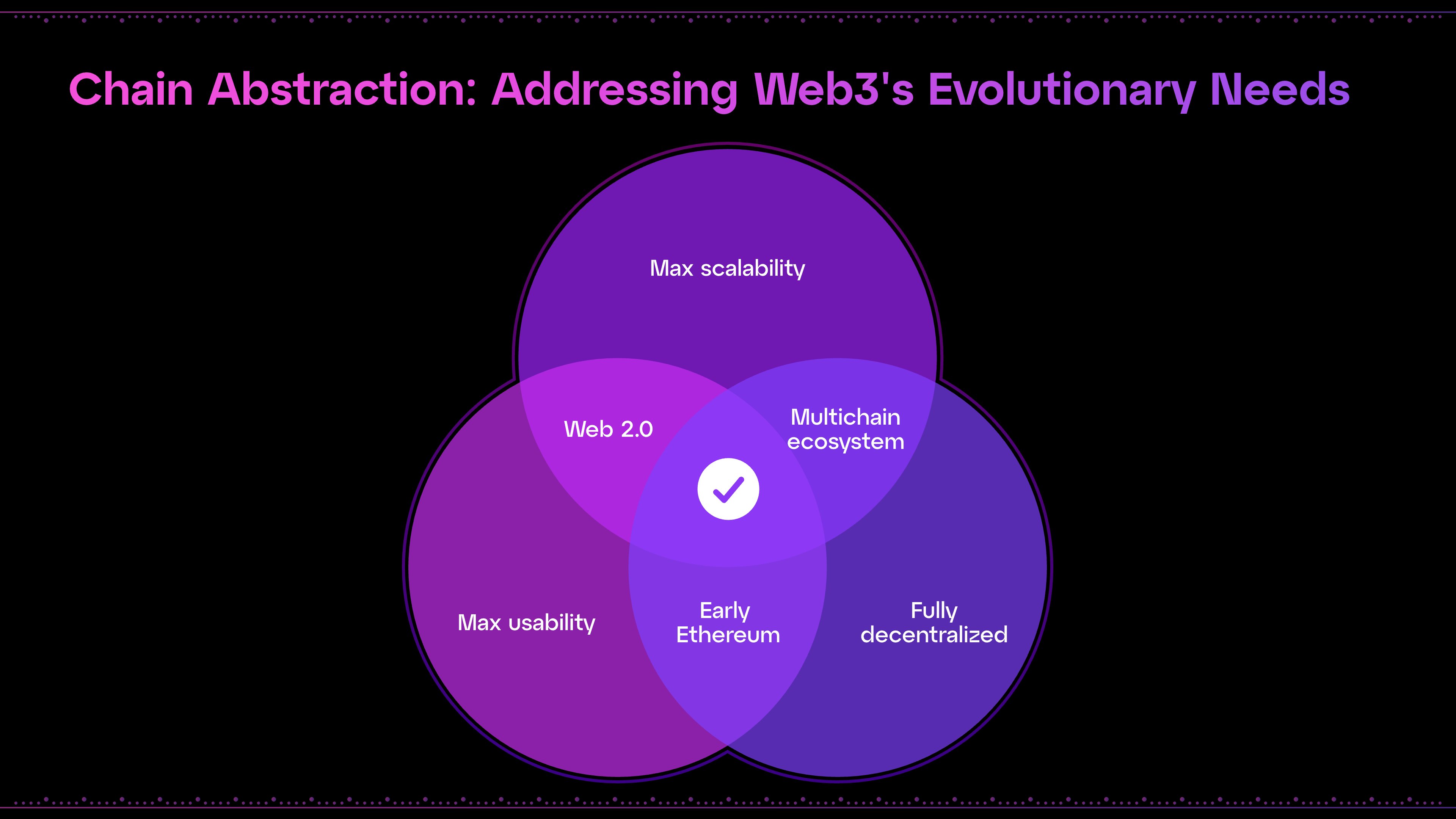
As a result of chain abstraction, Web3’s product offering and network effects can radically increase in both quantity and quality. This, in turn, will foster healthy competition among protocols in terms of products, not user bases. To accelerate chain abstraction, Particle Network is also collaborating closely with other industry players focused on this goal, including NEAR and the CAKE R&D group. As a guiding principle, we seek to establish standards and build upon existing solutions moving in the same direction, understanding our own solutions as a part of a larger picture.
Particle Network’s v1 Testnet –featuring Wallet, Liquidity, and Gas abstraction services– will be live shortly within Q2. After progressing to Mainnet, Particle’s aggregated DA and Dual Staking modules will be debuted in a Testnet version, progressing to Mainnet v2 before Q4 2024.
To stay informed about these upcoming announcements and learn more about our L1, follow us on our social media accounts below, or sign up for our newsletter by hitting “Subscribe”!
Particle Network's Wallet Abstraction solutions are 100% free for developers and teams. By integrating them, you can set your project in a path to leveraging chain abstraction.
About Particle Network

Particle Network powers chain abstraction, addressing Web3's fragmentation of users and liquidity. This is enabled by Particle's Universal Accounts, which give users a unified account and balance across all chains.
Share this article
About the author(s)






